|
Preferences |
Customize the appearance and behaviour of the program per your preferences:
- Colors palette
Choose a color scheme for the output window to be used throughout all IP-Tools utilities.
You can use standard Windows palette, green on black, yellow on blue, or light blue on blue.
- Fonts
Pick a font and set the desired font size.
- Help language
Select one of the languages in which help is available.
- Auto save main window options
If enabled, IP-Tools will save parameters of utilities (width of columns, current addresses, etc).
- Auto save current page
If selected, the program will be opening to the page last active in a previous session.
Otherwise "Local Info" page will be activated.
- Clear old info
If selected, IP-Tools will clear the output window before perform new test (everytime when you click "Start" button).
- Scroll down
If selected, IP-Tools will scroll down the output upon operation completed.
- Minimize to tray
Show icon in the tray when IP-Tools is minimized.
- Always on top
Unless minimized, the IP-Tools window remains on top of all other application windows.
- Keep recent addresses
Instructs IP-Tools to keep a history of recently used addresses.
|
|
Interface |
Interface options:
- Toolbar position
The IP-Tools toolbar can be configured to reside at the top or bottom of the window, or to be hidden away.
- Tabs position
The IP-Tools tabs can be configured to reside at the top or bottom of the window, or to be hidden away.
- Use multiple rows if needed
The IP-Tools tabs are lined up horizontally. If the application window is not wide enough to fit all of the tabs, two layout strategies are available. If this option is selected, the tabs are organized in as many rows as it takes to fit all of them. Otherwise, two scroll buttons appear at the right side of the tabs to allow you to scroll left and right..
- Status bar
Tells whether or not to display the Status bar
- When selecting the "Use List" option, show the Scan List dialog
Some of the IP-Tools utilities (NetBIOS, Lookup, all scanners) can use editable list of hosts.
With this option selected, checking the "Use List" option on the toolbar brings up the ScanList dialog.
|
|
HTML Colors |
Customize colors for HTML reports and log files.
|
|
Sound |
|
Use this panel to configure IP-Tools utilities to play sounds upon completion of certain operations.
|
|
Connection Monitor |
Connection list options
- Auto refresh
Specify an auto refresh interval.
- Save to log file
Specify the file to log events to.
- Display host names
Tells IP-Tools to resolve IP addresses to host names.
- Display port names
Tells IP-Tools to display symbolic port names rather than port numbers.
- Filter
Define selection criteria for connections to display based on their type and status.
- Address filter
Specify the addresses (or address ranges) you want to appear on or to be excluded from the list of current connections. Enter each address or a range of addresses on a separate line, as in the example below:
192.26.74.15
194.16.15.1 - 194.16.15.48
- Apply for
Specify whether the filter should be applied to the remote or local address, or to both.
|
|
NB Scanner |
NB Scanner options:
- Get host name before scanning
If enabled, the program tries to resolve the IP address into a host name prior to scanning its resources. If resolution fails and "Skip address if cannot be resolved" option is enabled, the program goes to the next host on the list.
- Skip address if cannot be resolved
Enable this option to skip addresses that cannot be resolved to host names
- Ping before scanning resources
If enabled, the program tries to ping the host prior to scanning its resources.
If the host does not respond and "Skip address if not responding" option is enabled, the program goes to the next host on the list.
For ping options see the Ping/Trace page in the Options dialog.
- Skip address if not responding
Enable this option to skip hosts that do not respond to echo packets
- Detect OS
If enabled, IP-Tools tries to detect the operationg system on the remote server. This option works on Windows NT/2000, and does not on Windows 9x/ME
- Scan resources
Searches for shared resources, like disks and printers, on the remote system
- Play sound when resource is found
You can specify a sound file (wav, mid, etc.) to play when a shared resource is found
|
|
SNMP Scanner |
Here you may administer SNMP Scanner settings.
Prior to scanning
Following options specify which preliminary checks should be made before performing basic SNMP requests:
- Ping before scanning resources
If enabled, IP-Tools tries to ping the host prior to performing SNMP requests. If the host does not respond
and "Skip address that is not responding" option is enabled, the program proceeds to the next host on the list.
For ping options see the Ping/Trace page in the Options dialog.
- Skip address that is not responding
Enable this option to skip hosts that do not respond to echo packets
- Get host name before scanning
If enabled, IP-Tools tries to resolve the IP address into a host name prior to performing SNMP requests. If name resolution fails and "Skip address that cannot be resolved" option is enabled, the program proceeds to the next host on the list.
- Skip address that cannot be resolved
Enable this option to skip addresses that cannot be resolved to host names
Scan options
Here you may specify parameters of basic SNMP queries:
- Port
Specify the port number on which the host (SNMP agent) is listening for incoming UDP packets. Default and
standard value is 161
- Timeout
This is the amount of time in milliseconds the program will wait for a response from the server before
considering the request as failed (if "Retries" parameter is greater than 1, scanner may perform several
requests).
- Retries
Specifies the communications retry count.
- Community strings
This option lists strings to utilize as SNMP community names while communicating with the hosts. To add new
string - click "Add item" button or press Insert key. To edit existing string - select the string in the
list and click "Edit item" button or double click on the string. To remove item - select the string and
click "Remove item" button. If you want to temporarily exclude some items from scanning process, unmark
the line.
You may select as many community strings as you wish. Remember though, the more strings you add, the longer
it could take for the scanner to discover network. SNMP Scanner tries to detect correct community string
for each device starting at the top of the list, so you should place the most commonly used community strings
at the very top of the list. You can rearrange the order of the community strings using the "Up" and "Down"
buttons.
Request additional information
In addition to standard requests that provide information about System ID, UpTime, Interfaces, etc, you may setup
IP-Tools to retrieve additional information. You may ask utility to request the value of any counter(s) supported
by SNMP agent.
To add a request field - click "Add item" button or press Insert key. In the popup dialog you should provide OID
(OBJECT IDENTIFIER) of the counter and the name of the field (name that will be displayed as column header in the
scanner utility, HTML report, etc). E.g. OID 1.3.6.1.2.1.4.1.0 addresses the counter that indicates whether host
is acting as an IP gateway or not.
To edit the field - select the item in the list and click "Edit item" button or double click on the item.
To remove item - select the line and click "Remove item" button. If you want to temporarily exclude some
requests from scanning process, unmark the line.
|
|
Port Scanner |
Port Scanner options:
- Get host name before scanning ports
If enabled, the program tries to resolve the IP address into a host name prior to scanning its ports.
If resolution fails and "Skip address if cannot be resolved" option is enabled, the program goes to the next host on the list.
- Skip address if cannot be resolved
Enable this option to skip addresses that cannot be resolved to host names
- Ping before scanning ports
If enabled, the program tries to ping the host prior to scanning its ports.
If the host does not respond and "Skip address if not responding" option is enabled, the program goes to the next host on the list.
For ping options see the Ping/Trace page in the Options dialog.
- Skip address if not responding
Enable this option to skip hosts that do not respond to echo packets
- Show only hosts with open ports
If this option is enabled, IP-Tools will not display any information for hosts with undetected open ports.
- Show port names
If enabled, meaningful port names are displayed beside port numbers.
- Show port descriptions
If enabled, a short description of each port is displayed.
- Timeout
IP-Tools offers 2 timeout options for Port Scanner:
- one timeout tells how long to wait for TCP connection;
- another timeout tells how long wait for data from server when "Show remote service messages" option enabled.
IP-Tools can send specific data to the open ports detected and display response from the remote system.
Use the following options to setup this feature:
- Show remote service messages
If enabled, IP-Tools waits for a response from the host and, unless timed out, displays the message received. If the option is disabled,
the program disconnects from the host immediately upon detecting an open port.
- Time for wait message
Specify how long to wait for a response.
- String to send to remote port
Specify a string to be sent to the remote host upon detecting an open port. You may use sequences formatted %XX where XX is a hexadecimal code of a character (byte).
E.g. HELLO%0D%0A would send HELLO
followed by a character ASCII 13 (line feed) and ASCII 10 (new line).
- Ports to scan
A list of ports to scan must be defined before scanning can happen. You can either specify a comma-separated list of ports and port ranges, like "21, 25, 43-80, 110-139", or click the "Select ports to scan" button to move to the Port List page.
|
|
Port List |
Use this page to select TCP ports to be tested by the Port Scanner utility.
What is a port ?
The TCP port number identifies a process or application inside the computer.
Any application or process that uses TCP for its transport is assigned a
unique identification number called a TCP port. These ports are numbered
beginning with zero. Port numbers for client applications are dynamically
assigned by the operating system when there is a request for service. Port
numbers for server applications are preassigned by the IANA
(Internet Assigned Numbers Authority) and do not change.
A server application or process that uses TCP as a transport has at least
one preassigned port number. For example, the preassigned port numbers for
FTP server services are 20 (data) and 21 (control).
|
|
UDP Scanner |
UDP Scanner's options:
- Get host name before scanning ports
If enabled, IP-Tools tries to resolve the IP address into a host name before scanning its ports. If
resolution fails and "Skip address if cannot be resolved" option is enabled, the program goes to the
next host in list.
- Skip address if cannot be resolved
Enable this option to skip addresses that cannot be resolved to host names.
- Ping before scanning ports
If enabled, IP-Tools tries to ping the host before scanning its ports. If the host does not respond and
"Skip address if not responding" option is enabled, the program goes to the next host in list. You can
setup ping parameters on the Ping/Trace page in the Options dialog.
- Skip address if not responding
Enable this option to skip hosts that do not respond to echo packets.
- Show only hosts with open ports
If this option is enabled, IP-Tools will not display any information for hosts with undetected open ports.
- Show port names
If enabled, meaningful port names are displayed beside port numbers.
- Show service reply
With this option enabled IP-Tools will display reply time or data received from the hosts for each active
UDP service detected. Using "Display", "From", and
"Till" parameters of the UDP check you can choose what
information IP-Tools should display for each type of UDP service (e.g. DNS, SNMP, etc)
- Show port descriptions
If enabled, a short description of each port is displayed.
- Timeout
Specify the amount of time (in milliseconds) that IP-Tools should wait for a response from the host.
- Retries
If IP-Tools does not receive answer from a host, it can send request again. Use this option to set the
number of times IP-Tools will resend the data to the server before consider that tested port is not in use.
Services to scan (UDP checks):
Use this list to select one or more UDP services to scan. You can mark/unmark services one by one or use special
buttons (located in the right bottom corner) to mark all services, unmark all services, or invert selections for
whole list.
IP-Tools contains list of some popular UDP services (Echo, Daytime, Chargen, Time, DNS, etc). If you need to
check UDP service that is not in the list, you can add new item. To create "check" for UDP service, click
"Add service" button and fill up following fields in the "UDP Service check" dialog:
- Port
Specify the port number on which the host is listening to incoming UDP packets. E.g. TFTP servers use port
#69, SNTP servers use port #123, Daytime servers use port #13, etc.
- Service name
Short name of the service
- Description
One line description of the service
- Packet to send
Enter the packet data that should be sent to the host. Because of the fact that most UDP services accept
binary data, you may need to use sequences formatted %XX where XX is a hexadecimal code of a character
(byte).
E.g. HELLO%0D%0A would send HELLO
followed by a character ASCII 13 (line feed) and
ASCII 10 (new line).
- Filter
By default IP-Tools displays any service the answer received from. But you can specify special filters for any
service "check". If data received from the service will not satisfy filter conditions, service will not be
considered as active one, and will not be listed in a list of active UDP services.
Choose one of the conditions to consider service's response as "good":
| - any reply | service that sends any data in response to request packet will be considered as active |
| - reply contains | service will be considered as the active one, only when reply contains specified data (defined in "Compare with" field). |
| - reply doesn't contain | service will be considered as the active one, only when reply does not contains specified data (defined in "Compare with" field). |
| - reply equal to | service will be considered as the active one, only when reply equal to specified data (defined in "Compare with" field). |
| - reply not equal to | service will be considered as the active one, only when reply not equal to specified data (defined in "Compare with" field). |
- Compare with
IP-Tools can compare data that was received from the server with specified string. As well as in
"Packet to send" field you can use sequences formatted %XX where XX is a hexadecimal code of a
character (byte). E.g. "%02public%00"
- Display
When "Show service reply" option is enabled, this parameter defines what information will be displayed when
active UDP service detected. Choose one of the following options:
- Reply time
- Reply as text
- Reply as binary data
- From/Till
Specify what part of the received data should be displayed. For example if you want to see 1st 5 bytes of the
service response, set "From" parameter to 1 and set "Till" parameter to 5. If you want to see service reply
starting from 10th symbol till 50th, set "From" and "Till" parameters to 10 and 50 correspondingly.
Examples:
To check TFTP service, fill up parameters with following values:
| - Port: | 69 |
| - Filter: | any reply |
| - Packet to send: | %00%01filename%00%00netascii%00
where filename is the name of the file on the server. We recommend provide incorrect (fake) name of the file (in this case server will not start file transfer, so you avoid unnecessary network traffic).
|
To check SNTP service fill up test parameters with following values:
| - Port: | 123 |
| - Filter: | any reply |
| - Packet to send: |
%0B%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00
%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00
%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00
Yes, string must be so long (48 bytes) |
|
|
Ping/Trace |
Use this page to define various ping/trace parameters:
- Packets to send
Specify the number of ECHO packets
- Packet size
Specify the size of ECHO packets
- Timeout
Specify a timeout interval in milliseconds
- Time To Live
Specify a TTL value
- Number of hops
Specify the maximum number of hops to reach the target
- Show host descriptions
If enabled, the program will display a description of the host beside host name
in the NS Lookup, Name Scanner, Port Scanner, Trace utilities.
Example:
... www.mit.edu (Massachusetts Institute of Technology)
... hnode51.telecom.tf (French Southern Territories)
... www.thaigov.go.th (Thailand)
- RMCP port
Ping Scanner can use ICMP and RMCP mode. In RMCP mode Remote Management Control Protocol is used to verify connection to remote servers.
Unlike ICMP Ping this mode may check powered off servers. Note: not every server supports RMCP and IPMI protocols.
Here you can specify the port number on which target hosts are listening for incoming RMCP/IPMI requests. Usually port 623 is used.
|
|
WhoIs |
IP-Tools has a built-in list of WhoIs servers for all top level domains.
You may create a custom list of your own, and its items will have priority over the built-in list servers.
The following proprties can be specified for each WhoIs server:
• Domain - domain, like ".com", or ".ibm.com"
• Comment - optional field, you can put any information into this field
• WhoIs server - WhoIs server address
• Port - port number (by defauld WhoIs servers use port 43)
• Max domain depth (domain level) supported - the maximum domain level supported by this server
• IP addresses are allowed in queries - mark this option if the server 'understands' IP addresses as well as host names
You could be a part of the community process to build up the WhoIs Server list. If you send us your custom list, it will be merged with contributions from other users, and an updated list will be sent back to you.
Click the "Update" button to initiate this process.
|
|
NS Lookup |
By default, the NS Lookup utility uses Windows API and the default DNS server to resolve IP addresses into host names, and vice versa. You can choose the "Advanced Name Server Lookup" option to turn NS Lookup into a powerful, versatile network administrator's utility.
In this case the following lookup parameters can be configured:
- DNS server address
- port number and transport protocol to use (TCP or UDP)
- timeout interval and number of retries
- type of request: A, ANY, CNAME, HINFO, MX, NS, PTR, SOA, or TXT
- enable or disable recursion
- output mode: Full, Medium, or Compact
IP-Tools supports the following request types:
- A - a host address
- NS - an authoritative name server
- MD - a mail destination
- MF - a mail forwarder
- CNAME - the canonical name for an alias
- SOA - marks the start of a zone of authority
- MB - a mailbox domain name
- MG - a mail group member
- MR - a mail rename domain name
- WKS - a well known service description
- PTR - a domain name pointer
- HINFO - host information
- MINFO - mailbox or mail list information
- MX - mail exchange
- TXT - text strings
|
|
HTTP |
On this page you can define parameters of HTTP requests performed by HTTP utility.
- Request
Choose type of the HTTP request:
- HEADER : request for HTTP header. Server will return status information about the document (HTTP header) but will not transfer data. It allows you to check web server functionality with minimum network traffic but you cannot check the content of the web page.
- GET: request the page specified by URL parameter. Server will return status information (HTTP header) and data.
- POST: send data (defined in "Post data" field) to the web server to be processed in some way, like by a CGI script. In this case URL is not a resource to retrieve; it's usually a program to handle the data you are sending. The HTTP response is normally the program output, not a static file. The most common use of POST is to submit HTML form data to CGI scripts.
- Post data
If the URL is for a POST request, enter the post variables as
name1=value&name2=value2. This option is used
to verify that a form is working correctly by performing the same request which occurs when a user submits a
form.
- Follow redirect
This parameter determines the IP-Tools' behavior, when the server issues a redirect. When the option is enabled
IP-Tools follows redirect and retrieves new URL, specified by server.
Authorization
- User name
If the URL specified requires a name and password for access, enter the user name in this box.
- Password
If the URL specified requires a name and password for access, enter the password in this box.
Proxy
Optionally, a proxy server can be used to access the URL. Setup following parameters:
- Proxy address
Provide a domain name or IP address of the proxy server
- Proxy port
Specify TCP port used by proxy server
Proxy authorization
- User name
If the proxy server requires a name and password for access, enter the user name in this box.
- Password
If the proxy server requires a name and password for access, enter the password in this box.
- Agent
Some server-based scripts can check agent's name and return different information for different HTTP
agents (e.g. generate different HTML pages for Internet Explorer or Netscape). You can change this parameter
to check functionality of the script in different modes.
- Timeout
Specify the number of seconds that the IP-Tools should wait for a page to complete downloading before
timing-out. If the Timeout property is set to 0, IP-Tools will use default Windows timeout specified for
TCP protocol.
- Display HTTP header and HTML tags
With this option enabled IP-Tools displays all data received from the server as it is. If you disable the
option, IP-Tools will not display HTTP header and will remove all HTML tags from the response.
- Allow per-session cookies
With this option enabled IP-Tools remembers cookies received from the server, and sends them back in case of
redirection to another URL.
This option can be useful when you need to check some access-restricted resources. Often web-based
authorization systems use cookies to identify user. How it usually works:
- user opens login page, enters login and password, and clicks "Login" button;
- browser sends POST or GET request to a server with data entered by user;
- server checks login/password and (in case data are correct) assings session ID for the user;
- server sends cookie that contains ID to user's browser, and redirects user to another page;
- browser must store cookie and send it back to server every time it (browser) requests access-restricted pages
So, IP-Tools can work like your browser and (just for example) login to your mailbox to check whether you
have the new messages.
|
|
IP-Monitor |
Customize the appearance of IP-Monitor by selecting a refresh interval, color scheme, and number of grids for different activity charts.
|
|
Host Monitor |
Specify the following Host Monitor options::
Style:
- Report - a small icon and detailed host information is displayed for each host on the list
- List - a small icon and the host name is displayed
- Icon - a large icon and the host name (names may have to be cut)
- Small Icon - modified version of the List style ;-) Try it and see
Show grid lines
Specify whether you want the gridlines separating task items to be visible.
Start/Stop mode:
- Start upon loading
- Stop upon loading
- Restore last status
Refresh options:
- Always check status when host properties are changed
- Ask confirmation before checking status
- Do not check status when host properties are changed
|
| Host Monitor: Log settings |
Specify Host Monitor log file settings:
Log file
- Log to the file
- Automatically change file name every month
- Automatically change file name every day
- Disable logging
If an option to automatically change the file name is selected, a template can be specified for the file name.
Host monitor interprets the text between percentage marks (%) as macros.
The following macros are supported: 'DD' represents the day of the month; 'MM' - the month; 'YY' - the last two digits of the year, 'YYYY' - the year.
Examples:
c:\hostmon\log\%ddmmyy%.dbf - HostMonitor writes the log to
the c:\hostmon\log\ directory and changes the name of log file every day.
%yyyy%.htm - writes the log to the current directory (not a good idea as the current directory may change) and changes the name of the log file every year.
Save mode
- Save all information
- Save only if host changes status
If the "Save all information" option is selected, HostMonitor will save the results of all tests in a log file (even if the status of a host does not change).
This mode is useful to create detailed statistical information about access time to hosts.
However, using this mode will significantly increase the size of the log file.
Log file format
Note:
HTML logs need more disk space (about 800 bytes per record) than text log files (about 80 bytes per record),
but HTML logs are more visual and can be linked to a web server's folder and read from anywhere.
|
|
Trap Watcher |
|
Here you may specify general Trap Watcher settings and provide special processing options for all or some messages.
E.g. you may log all messages but send an e-mail only when message from specific device is received. Or you may
display all messages on screen and log [Link Down] and [Link Up] messages.
Receive traps on UDP port #
This option specifies the UDP port number, which IP-Tools utilizes to listen for incoming messages. Default setting is 162.
Display
This option allows you to specify how many latest messages should be displayed on screen. Also you may specify what messages should be displayed:
- Display all received traps
All received messages will be displayed
- Display filtered traps only
Only messages that meet conditions of the filter will be displayed
- Display all traps, mark filtered
All received messages will be displayed, messages that meet conditions of the filter
will be marked by color (you can choose any color you want)
By clicking on "Date" column header you may change sorting mode for messages; newest messages could appear at the
top or bottom of the list.
Log
IP-Tools can log all or some specific messages into log file or files. Choose one of the following options:
- Log all traps
All received messages will be stored
- Log filtered traps
Only messages that meet conditions of the specified filter will be stored
- Disable logging
No messages will be stored in the log
IP-Tools may store information in Text or HTML format. If you provide path to the file with extension HTM or HTML,
IP-Tools will create HTML log file. Otherwise log will be in text format.
You may use special macro variables in the file name. This option allows you to create
separate log files for various messages. E.g. If you use %TrapHost% variable in the file name, IP-Tools will
create separate log file for each host from which a trap messages was received.
Execute external command
Here you may specify command that will be executed when any or specified message is received. Choose one of the following options:
- For all traps
Execute command in respond to every new message
- For filtered traps
Execute command in respond to messages that meet conditions of the filter
- Do not execute
Do not execute external programs
and provide command line to execute. You may use special macro variables in the command
line. When IP-Tools launches external application in response to received trap message, it substitutes macro
variable with its value pertinent to the trap message being received.
Macro variables
You may use special variables in the log file name or in the command line to launch external applications:
| %TrapHost% | Represents IP address of the host that have sent the message |
| %TrapType% | Represents type of the trap. It provides information about generic type and enterprise specific number. Generic type could be one of the following: Cold Start, Warm Start, Link Down, Link Up, Auth Failure, EGP Loss and Specific. Enterprise specific number is only applicable when generic trap type is Enterprise Specific, otherwise enterprise specific number is 0 |
| %TimeTicks% | Represents time ticks. Time ticks is the time interval (measured in hundredth of seconds) since the initialization (boot, start-up) of the entity that have sent the trap. |
| %Enterprise% | Enterprise field contains an OBJECT IDENTIFIER which names the device that sends the trap |
Each trap message may contain one or several variables that provide information about the event. Following macro variables allow you to pass that information to external applications. |
| %MibOid% | Represents variable name (OID) |
| %MibType% | Type of the variable |
| %MibValue% | Variable value |
| %MibRelative% |
Relative value of the variable. This macro is applicable when you check incoming trap messages for some
specific variable and compare current value of the variable with its previous value (see
"Message contains OID" option in the Trap Filter dialog).
%MibRelative% may represent:
- simple difference between current and previous value (if you use "increases by", "decreases by" or "changes by" compare option)
- relative difference as a percentage of previous value (if you use "increases by (%)", "decreases by (%)" or "changes by (%)" compare option)
- average increase/decrease of the counter per second since previous message (if you use "increases /sec", "decreases /sec" or "changes /sec" compare option)
|
When IP-Tools launches external application in response to received trap message, it substitutes macro variable
with the value of the appropriate message parameter.
E.g. to send an e-mail with information about traps you may use command line similar to this one:
"c:\program files\IP-Tools\samples\SendMail.exe" "To=admin@mycompany.com" "Subject=SNMP trap message from %TrapHost%"
"Body=OID: %MibOID% ^M Value: %MibValue%" StartAfterLoad
Using variables in the log file name allows you to store different messages in separate log files. E.g. If you
use %TrapHost% variable in the file name, IP-Tools will create separate log file for each host from which a
trap messages was received.
You may setup filter and provide special processing for some messages. E.g. you may log all messages but send
an e-mail only when message from specific device is received. Or you may display all messages on screen and log
[Link Down] and [Link Up] messages.
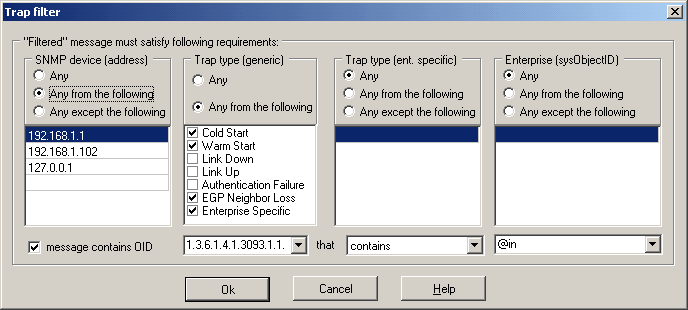
In the Trap Filter dialog you may define one or more conditions to filter some specific events. Message passes the
filter only when it matches ALL specified requirements:
SNMP device
Match against the source device - device that have sent message. You can provide list of IP addresses and choose one of the following options:
|
| messages from any device will be accepted |
| messages only from specified devices will be accepted |
| messages from any devices except specified will be accepted |
List editing tips
- To add new items to the end of the list go to the last existing line and press Down Arrow key.
- Press INSERT key to insert new item.
- Press CTRL+DEL to remove item.
- Press F2 to edit item.
Trap type (generic)
Match against the generic type of the trap:
|
| select this option to accept messages of any type. |
|
if you want to accept just some type of messages, select this option and mark one or several possible event
types: Cold Start, Warm Start, Link Down, Link Up, Authentication Failure, EGP Neighbor Loss, Enterprise Specific
- Cold Start - the sender is reinitializing and its configuration may change
- Warm Start - the sender is reinitializing but its configuration will not change
- Link Down - failure in one of the agent's links
- Link Up - one of the agent's links has come up
- Authentication Failure - the agent received a protocol message improperly authenticated
- EGP Neighbor Loss - an Exterior Gateway Protocol neighbor is down
- Enterprise Specific - the trap is identified as not being one of the basic traps
|
Trap type (specific)
You can provide list of enterprise specific codes (numbers) and choose one of the following options:
|
| accept messages of any type |
| accept only messages that have one of the specified enterprise specific types |
| accept messages with any enterprise specific type except those that are specified in the list |
List editing tips
- To add new items to the end of the list go to the last existing line and press Down Arrow key.
- Press INSERT key to insert new item.
- Press CTRL+DEL to remove item.
- Press F2 to edit item.
Enterprise (not applicable for SNMPv2 Traps)
Enterprise field of the trap contains an OBJECT IDENTIFIER, which names the device that sends the trap. Here you may provide list of OIDs and choose one of the following options:
|
| do not check Enteprise field of the traps |
| accept only messages from listed devices. |
- Any except the following accept
| all messages except from the devices on the list |
|
Message contains OID
This option allows you to check incoming trap messages for some specific variable and
• compare its value to some constant (string or numeric)
• compare current value of the variable with previous value of this variable
Just provide OID (OBJECT IDENTIFIER) of the variable and choose one of the following compare conditions:
| • is < than | message fits the condition when value of the variable is less than specified number |
| • is > than | message fits the condition when value of the variable is greater than specified number |
| • is = to | message fits the condition when value of the variable is equal to specified number or string |
| • is <> from | message fits the condition when value of the variable is not equal to specified number or string |
| • contains | message fits the condition when value of the variable contains specified string |
| • does not contain | message fits the condition when value of the variable does not contain specified string |
| Also Trap Watcher has 9 conditions that allows you to check how new value had changed versus its previous value: |
| • increases by | trap message fits the condition when new value is greater then the old one by specified number or more |
| • decreases by | message fits the condition when new value is less then old one by specified number or more |
| • changes by | message fits the condition when absolute difference between new and old value is equal or greater then specified number |
| • increases by (%) | message fits the condition when new value had increased by specified (or greater) percentage versus the old one |
| • decreases by (%) | message fits the condition when new value had decreased by specified (or greater) percentage versus the old one |
| • changes by (%) | message fits the condition when an absolute difference between new and old values measured as a percentage of an old value is equal or greater then specified percentage number |
| • increases /sec | message fits the condition when average increase of the counter (per second) is greater than the specified limit ((current value - old value)/elapsed time >= specified limit) |
| • decreases /sec | message fits the condition when average decrease of the counter (per second) is greater than the specified limit ((old value - current value)/elapsed time >= specified limit) |
| • changes /sec | message fits the condition when average absolute difference (change) of the counter (per second) is greater than the specified limit (abs(current value - old value)/elapsed time >= specified limit) |
|
If you use relative compare modes (increases by, changes by, decreases by (%), increases /sec, etc)
and various network sources can send the same variable, you should restrict the filter to accept SNMP Trap
messages from a single source only. Otherwise IP-Tools could compare messages received from different sources
(that usually does not make any sense).
|
|
Scan List |
On this page you can define a list of addresses that can be used by the NetBIOS, NB Scanner, SNMP Scanner,
Name Scanner, Port Scanner, UDP Scanner, Ping Scanner, and LookUp utilities. You can define one list for
all utilities or specify a separate list for each utility.
Enter list items one per line as:
- host names (like "www.yahoo.com");
- IP addresses (like "123.54.123.145");
- ranges of IP addresses (like "198.201.73.2 - 198.201.74.254");
- comments, separated by semicolon (;).
Example :
;------------------------------------------------------------------------
; IP-Tools ignores text after ';'
133.65.12.250 - 133.65.13.17 ; You may use range of IP addresses, e.g.
200.32.12.88 - 200.32.12.95 ; correct
200.32.12.22 - 200.32.12.25 ; correct
;www.aris.com - www.yahoo.com ; wrong!
www.mydom.net ; for single host you may use hostname
www.yahoo.com ; correct
199.66.10.12 ; correct
199.66.10.15 ; correct
;------------------------------------------------------------------------
|